For working professionals
For fresh graduates
- Study abroad
More
- Executive Doctor of Business Administration from SSBM
- Doctorate in Business Administration by Edgewood College
- Doctorate of Business Administration (DBA) from ESGCI, Paris
- Doctor of Business Administration From Golden Gate University
- Doctor of Business Administration from Rushford Business School, Switzerland
- Post Graduate Certificate in Data Science & AI (Executive)
- Gen AI Foundations Certificate Program from Microsoft
- Gen AI Mastery Certificate for Data Analysis
- Gen AI Mastery Certificate for Software Development
- Gen AI Mastery Certificate for Managerial Excellence
- Gen AI Mastery Certificate for Content Creation
- Post Graduate Certificate in Product Management from Duke CE
- Human Resource Analytics Course from IIM-K
- Directorship & Board Advisory Certification
- Gen AI Foundations Certificate Program from Microsoft
- CSM® Certification Training
- CSPO® Certification Training
- PMP® Certification Training
- SAFe® 6.0 Product Owner Product Manager (POPM) Certification
- Post Graduate Certificate in Product Management from Duke CE
- Professional Certificate Program in Cloud Computing and DevOps
- Python Programming Course
- Executive Post Graduate Programme in Software Dev. - Full Stack
- AWS Solutions Architect Training
- AWS Cloud Practitioner Essentials
- AWS Technical Essentials
- The U & AI GenAI Certificate Program from Microsoft
1. Introduction
6. PyTorch
9. AI Tutorial
10. Airflow Tutorial
11. Android Studio
12. Android Tutorial
13. Animation CSS
16. Apex Tutorial
17. App Tutorial
18. Appium Tutorial
21. Armstrong Number
22. ASP Full Form
23. AutoCAD Tutorial
27. Belady's Anomaly
30. Bipartite Graph
35. Button CSS
39. Cobol Tutorial
46. CSS Border
47. CSS Colors
48. CSS Flexbox
49. CSS Float
51. CSS Full Form
52. CSS Gradient
53. CSS Margin
54. CSS nth Child
55. CSS Syntax
56. CSS Tables
57. CSS Tricks
58. CSS Variables
61. Dart Tutorial
63. DCL
65. DES Algorithm
83. Dot Net Tutorial
86. ES6 Tutorial
91. Flutter Basics
92. Flutter Tutorial
95. Golang Tutorial
96. Graphql Tutorial
100. Hive Tutorial
103. Install Bootstrap
107. Install SASS
109. IPv 4 address
110. JCL Programming
111. JQ Tutorial
112. JSON Tutorial
113. JSP Tutorial
114. Junit Tutorial
115. Kadanes Algorithm
116. Kafka Tutorial
117. Knapsack Problem
118. Kth Smallest Element
119. Laravel Tutorial
122. Linear Gradient CSS
129. Memory Hierarchy
133. Mockito tutorial
134. Modem vs Router
135. Mulesoft Tutorial
136. Network Devices
138. Next JS Tutorial
139. Nginx Tutorial
141. Octal to Decimal
142. OLAP Operations
143. Opacity CSS
144. OSI Model
145. CSS Overflow
146. Padding in CSS
148. Perl scripting
149. Phases of Compiler
150. Placeholder CSS
153. Powershell Tutorial
158. Pyspark Tutorial
161. Quality of Service
162. R Language Tutorial
164. RabbitMQ Tutorial
165. Redis Tutorial
166. Redux in React
167. Regex Tutorial
170. Routing Protocols
171. Ruby On Rails
172. Ruby tutorial
173. Scala Tutorial
175. Shadow CSS
178. Snowflake Tutorial
179. Socket Programming
180. Solidity Tutorial
181. SonarQube in Java
182. Spark Tutorial
189. TCP 3 Way Handshake
190. TensorFlow Tutorial
191. Threaded Binary Tree
196. Types of Queue
197. TypeScript Tutorial
198. UDP Protocol
202. Verilog Tutorial
204. Void Pointer
205. Vue JS Tutorial
206. Weak Entity Set
207. What is Bandwidth?
208. What is Big Data
209. Checksum
211. What is Ethernet
214. What is ROM?
216. WPF Tutorial
217. Wireshark Tutorial
218. XML Tutorial
Splunk Tutorial for Beginners
Understanding the data analysis domain can be exciting and overwhelming, especially for beginners. In our comprehensive splunk tutorial for beginners, we will guide you through the intriguing world of data exploration.
Throughout this tutorial, we'll unravel the fundamental concepts of Splunk, a robust platform that transforms raw data into actionable insights. We'll begin with the splunk basics, introducing you to the core functionalities and terminology. From there, we'll delve into data ingestion, showing you how to bring various data sources into Splunk for analysis.
What is Splunk?
Splunk is a versatile and powerful data platform that enables organizations to turn raw data into valuable insights. It is widely used for analyzing, monitoring, and visualizing data from different sources to gain actionable intelligence and make informed decisions. With its robust capabilities, Splunk is a go-to tool for IT operations, security, business intelligence, and more.
Examples of Splunk Use Cases:
- IT Operations Monitoring: Organizations use Splunk to monitor their IT infrastructure, servers, networks, and applications. For instance, a company might use Splunk to identify performance bottlenecks in their web servers by analyzing log data.
- Security Information and Event Management (SIEM): Splunk is often used for security analysis. For example, it can identify unusual login patterns that might indicate a cyber attack.
- Business Intelligence: In the business context, Splunk can be used to analyze customer behavior, sales trends, and operational efficiency. Retailers might analyze purchasing patterns to optimize inventory management.
- Internet of Things (IoT) Monitoring: Splunk can collect and analyze data from IoT devices. For instance, a manufacturer could monitor sensor data from machinery to predict maintenance needs and prevent downtime.
- Application Performance Monitoring: Organizations can monitor the performance of their applications, identify errors, and optimize user experiences by analyzing application logs and metrics.
Splunk's flexibility and adaptability make it a valuable asset across various industries and use cases, helping organizations make sense of their data and generate insights that drive better decision-making.
Splunk Versions
Within the dynamic data analytics landscape, Splunk emerges as a versatile and transformative platform catering to a spectrum of organizational needs. Tailoring its offerings to diverse use cases, Splunk provides a range of versions that empower businesses to unravel insights hidden within their data streams. From intricate IT operations to robust security analysis and beyond, each version of Splunk serves as a gateway to informed decision-making.
Let's delve into this tapestry of Splunk versions:
- Splunk Free: Where exploration begins, offering limited yet impactful capabilities, making it the perfect launchpad for small-scale data analysis.
- Splunk Enterprise: The pinnacle of Splunk's prowess, Enterprise is helping enterprises grapple with vast and complex data landscapes. Deployable on-premises or in the cloud, it's a cornerstone of IT operations, security, and beyond.
- Splunk Cloud: Seamlessly merging power and convenience, this version brings Splunk's prowess to the cloud realm, removing the burden of on-premises maintenance.
- Splunk Light: An elegant solution tailored for smaller IT environments, providing essential indexing and search functions.
- Splunk IT Service Intelligence (ITSI): Navigating the intricate world of IT services, this version clarifies service performance and offers insights for effective infrastructure management.
- Splunk Security Solutions: Safeguarding with precision, Splunk's security-focused versions, including Enterprise Security (ES) and User Behavior Analytics (UBA), stand guard against threats and unearth critical patterns.
- Splunk Observability Suite: Ensuring holistic insights, this suite orchestrates Infrastructure Monitoring, APM, and Synthetic Monitoring, delivering end-to-end observability for applications and infrastructure.
- Splunk Industrial Asset Intelligence (IAI): This version empowers organizations to monitor, assess, and optimize industrial systems and machinery.
- Splunk Data Stream Processor (DSP): For real-time analytics, DSP reigns supreme, enabling organizations to harness the potential of streaming data with efficiency.
- Splunk Phantom: A symphony of security orchestration and automation, Phantom streamlines security operations for rapid response.
Features of Splunk
Splunk is renowned for its rich features enabling organizations to analyze and derive insights from their data. Here are some key features of Splunk, along with examples to illustrate how they work:
- Data Collection
Splunk allows you to collect data from various sources, such as logs, metrics, events, and more. This data can come from applications, servers, devices, and external systems.
Example: A web server generates log files containing information about user requests, response times, and errors. Splunk can collect and index these log files for analysis.
- Indexing and Search
Splunk indexes the collected data, making it searchable and retrievable at high speeds. Users can then search, filter, and analyze this indexed data.
Example: An IT team uses Splunk to index and search through server logs to identify the root cause of a performance issue.
- Real-time Analysis
Splunk enables real-time data analysis, allowing users to monitor ongoing events and trends as they happen.
Example: A security team monitors network traffic in real time using Splunk to detect and respond to potential cyber threats.
- Search Processing Language (SPL)
SPL is a powerful query language that allows users to perform complex searches, calculations, and statistical analysis on their data.
Example: A business analyst uses SPL to calculate the average purchase amount per customer and create visualizations to analyze buying patterns.
- Visualizations and Dashboards
Splunk provides tools to create visualizations like charts, graphs, and maps. Dashboards can be built to showcase these visualizations, making it easier to understand and communicate insights.
Example: An operations team creates a dashboard displaying real-time server performance metrics, helping them quickly identify anomalies.
- Alerting and Notifications
Splunk can trigger alerts based on specific conditions or patterns in the data. These alerts can be sent via email, SMS, or integrated with other communication systems.
Example: A system administrator sets up an alert to notify them when server CPU usage exceeds a certain threshold.
- Machine Learning and AI Integration
Splunk integrates machine learning and artificial intelligence capabilities to identify patterns, anomalies, and trends in data.
Example: An e-commerce company uses machine learning in Splunk to predict customer churn based on historical behavior and demographics.
- Data Enrichment and Transformation
Splunk allows you to enrich and transform data during indexing, adding context and making it more valuable for analysis.
Example: An IoT application enriches sensor data with location information to analyze how environmental factors impact machine performance.
- Universal Forwarders
Universal forwarders are lightweight agents that collect and send data to the Splunk indexers.
Example: A mobile app developer uses a forwarder to send user behavior data from the app to Splunk to analyze user interactions.
These features collectively empower organizations to gain insights, improve decision-making, enhance security, and optimize their operations using data-driven approaches.
Lookups in Splunk
In Splunk, "lookups" refer to a powerful feature that allows you to enrich or modify your data by referencing external data sources. Lookups provide a way to combine data from different sources, enhancing the context and value of your analysis.
This feature is handy when you want to associate additional information with your events or perform more complex analysis that requires data correlation.
Here's a breakdown of lookups in Splunk:
- What Are Lookups Used For?
Lookups are used to add fields or values to your events based on matching data in an external table or file. This can be incredibly useful for:
- Enrichment: Adding additional details to your events. For example, mapping IP addresses to geographic locations or correlating user IDs with employee names.
- Data Correlation: Combining data from different sources based on common fields. For instance, associating customer IDs from your logs with customer information from a CRM system.
- Types of Lookups
Splunk supports various types of lookups, including:
- CSV Lookups: These involve referencing data from a CSV (Comma-Separated Values) file that you upload to Splunk. This is a common method for smaller datasets.
- KV Store Lookups: Using Splunk's internal key-value store to perform faster and more scalable lookups.
- External Lookup Scripts: Running custom scripts (Python, Perl, etc.) to perform more complex lookups involving external databases or APIs.
Splunk query language
Splunk Query Language (SPL) is a powerful and flexible language used to search, analyze, and extract insights from your data in Splunk. It enables you to perform a wide range of operations on your data, from simple searches to complex analysis and reporting. SPL is designed to help you explore and transform your data to find patterns, anomalies, trends, and more.
Here's an overview of some key aspects of SPL:
- Basic Structure:
SPL queries are typically composed of commands followed by arguments, field names, and values. Commands are separated by pipe (|) characters to create a pipeline of operations.
- Searching and Filtering:
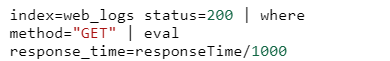
You can use commands like search, where, and eval to filter and manipulate your data. For example:
- Field Extraction:
SPL allows you to extract fields from your data using the rex or spath command. This is useful when you want to isolate specific pieces of information within your events.
- Aggregation and Statistics
SPL offers commands like stats, chart, timechart, and top to perform aggregation and generate statistical summaries of your data.
- Time-Based Analysis:
A time-based analysis is crucial in Splunk. You can use time-related commands like timechart to visualize data trends over time.
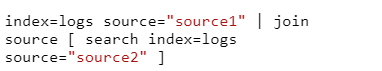
- Joining and Merging Data:
SPL lets you combine data from different sources using commands like join and appendcols.
- Subsearches
You can use subsearches to use the results of one search as input for another.
Splunk Commands
Splunk offers a wide range of commands you can use in the Splunk Query Language (SPL) to search, filter, transform, and analyze your data. These commands are the building blocks for constructing queries and extracting insights from your data. The following are some commonly used Splunk commands, along with brief explanations:
- search: The primary command used to initiate a search. It retrieves events from the specified index or indexes based on your search criteria.
- table: Displays results in a tabular format, showing specific fields from the events.
- stats: Computes statistics, aggregations, and summaries of your data. You can use functions like count, sum, avg, etc.
- timechart: Generates time-based visualizations, such as line charts, bar charts, or area charts, to display data trends over time.
- eval: Creates new fields or modifies existing fields using calculations or transformations.
- where: Filters events based on specified conditions.
- rex: Extracts fields using regular expressions.
- transaction: Groups events together based on a shared field or condition, forming transactions.
- join: Combines events from different sources based on common fields.
Conclusion
In the ever-evolving landscape of data analytics, Splunk stands as a beacon of transformation, empowering organizations to harness the power of their data like never before. With its array of features and capabilities, Splunk has become a cornerstone for diverse industries, paving the way for informed decision-making, enhanced security, and operational excellence.
From the moment data is collected to the creation of insightful visualizations, Splunk orchestrates a seamless journey through the intricacies of data analysis. It transforms raw data into actionable insights, revealing hidden patterns, trends, and anomalies that might otherwise go unnoticed.
As we've explored the key features of Splunk, from its real-time analysis prowess to its ability to turn data into meaningful visual stories, it's evident that Splunk is not just a tool, but a strategic asset for organizations striving to thrive in a data-driven world.
FAQs
- How does Splunk handle data security and privacy?
Splunk prioritizes data security and privacy with encryption, role-based access control, and data masking. It ensures secure token authentication and integrates with authentication providers like LDAP and SAML.
- How can Splunk be used for business intelligence and reporting?
Splunk extends beyond IT to drive business insights. It analyzes sales, customer interactions, etc., offering visualization tools and dashboards for creating informative reports.
- How can machine learning be integrated into Splunk for advanced analysis?
Splunk's Machine Learning Toolkit (MLTK) enables predictive analysis and anomaly detection. Users can build custom models, detect patterns, and predict outcomes without extensive data science expertise.

Author|900 articles published


upGrad Learner Support
Talk to our experts. We are available 7 days a week, 9 AM to 12 AM (midnight)
Indian Nationals
1800 210 2020
Foreign Nationals
+918068792934
Disclaimer
1.The above statistics depend on various factors and individual results may vary. Past performance is no guarantee of future results.
2.The student assumes full responsibility for all expenses associated with visas, travel, & related costs. upGrad does not provide any a.